Know the Intent. Control the Action.
ArmorIQ uses Intent Intelligence™ to interpret agent goals, verify identity and access, and enforce policies at runtime - keeping agents safe and compliant

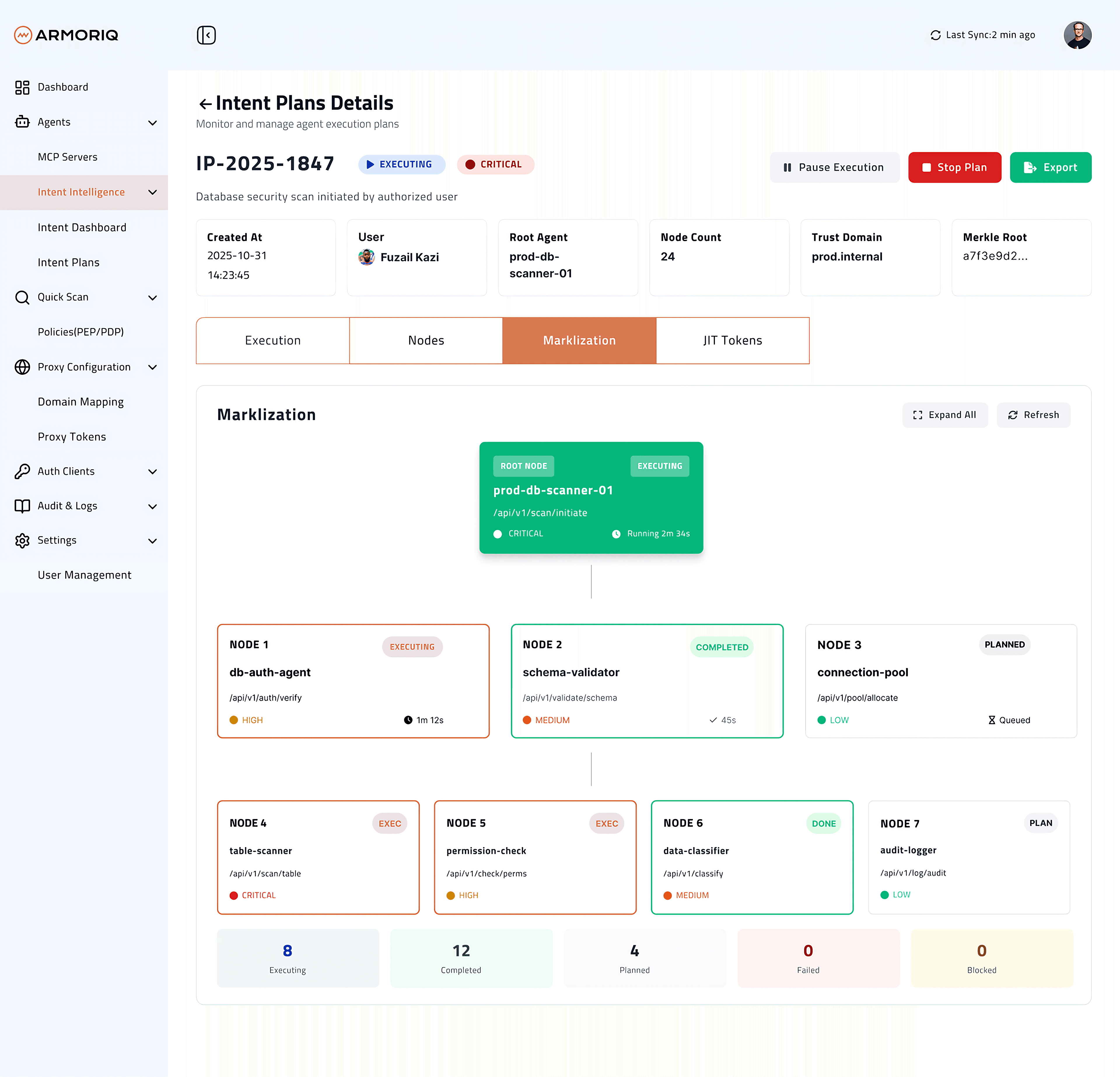
Why ArmorIQ Changes Everything
Control Where It Matters: The Intent Layer
AI agents decide before they act.
ArmorIQ captures intent with Intent Intelligence™, shapes plans, and applies guardrails before execution, so actions stay aligned with policy and business goals.
The Identity Fabric for Autonomous Agents
Traditional IAM wasn't built for AI.
ArmorIQ delivers agent-native identity, delegated authority, lifecycle controls, and cross-domain trust, so agents can operate safely across systems.
Continuous Visibility Across the Agentic Surface
MCP servers, tools, schemas, and A2A interactions, ArmorIQ sees it all.
Track every surface an agent can access, call, or traverse, with clear traces across workflows and systems.
Real-Time Compliance for Agentic Systems
No more guessing. No more manual reviews.
ArmorIQ automatically captures evidence from agent activity and produces compliance-ready records, so teams can prove controls continuously.
Everything You Need to Run AI Agents Safely
Identity, intent, controls, and visibility. Built for the enterprise

Intent Intelligence™ Engine
Policy-aware decisioning for AI agents
Monitors agent reasoning, evaluates planned actions against access and policy, and enforces safe execution across tools and data
- Pre-execution intent capture
- Execution graph modeling
- Real-time alignment enforcement
- Policy-aware reasoning

Sentry
Protect every agent entry point
Maps MCP servers, tools, schemas, and A2A routes, continuously checks configuration, detects drift, and surfaces risk across agent infrastructure.
- MCP server discovery
- Configuration scanning
- Drift detection
- Continuous monitoring
Gatekeeper
Strong identity and least-privilege for agents
Issues and manages agent identities, scopes delegated permissions, enforces on-behalf-of flows, and supports secure access across domains
- Agent identity management
- Delegated authority control
- On-behalf-of enforcement
- Cross-domain trust

Registry
The system of record for your agent ecosystem
A centralized catalog of agents, MCP servers, tools, schemas, dependencies, provenance signals, and runtime state, kept current as things change
- Complete agent catalog
- Dependency mapping
- Provenance tracking
- Runtime state management

Auditor
Real-time proof for agent activity
Captures evidence automatically, links actions to required controls, and produces defensible reports, so compliance is always current.
- Continuous evidence collection
- Framework mapping
- Audit-ready reporting
- Action defensibility
Frequently Asked Questions
Everything you need to know about ArmorIQ and Intent Assurance
Intent is the explicit purpose behind an AI action. It defines what the system is meant to do, within what scope, and with what limits. AI agents reason dynamically, so intent cannot be assumed it must be declared and enforced.
Intent Assurance ensures that every AI action is verified against an approved purpose before it executes. If an action does not belong to the declared intent, it is blocked. This prevents silent drift, unintended escalation, and unauthorized outcomes.
IAM verifies who can act and what they can access. Intent Assurance verifies whether the action should happen at all. AI systems can be fully authenticated and still act incorrectly. Intent Assurance closes that gap.
ArmorIQ sits between AI reasoning and execution. Agents can plan and adapt freely, but before any action runs, ArmorIQ checks that it aligns with approved intent. It builds on to complement existing IAM, Zero Trust, and monitoring. It does not replace them.
ArmorIQ is for teams accountable when AI systems act. That includes platform leaders, SREs, and security teams, anyone who is managing irreversible actions. Most teams don't look for Intent Assurance at first they realize they need it once autonomy becomes real.

If You Can't Control Agents, You Can't Trust Them.
Join the companies setting a safer standard for agent deployments.